TLS/SSL
The web server supports TLS (Transport
Layer Security) and SSL (Secured Socket Layer) protocols which provide site
authentication and content encryption. On web browsers, users can access to the
device by using https:// prefix before the device��s URL.
Protocols:
TLS1, SSL3
SSL2 is disabled for security consideration
Browser
Compatibility:
|
Browser |
HTTP (boa) |
HTTPS (boa-ssl) |
|
Microsoft IE6,
IE7, IE8 |
|
|
|
Mozilla Firefox 3.0,
3.5 |
|
|
|
Google Chrome 2 |
|
|
|
Apple Safari 4 |
|
|
|
Opera 10 |
|
|
|
Microsoft IE5,
IE5.5 |
|
|
|
Mozilla 1.2, 1.4 |
|
|
|
Microsoft IE4 |
|
|
The TLS/SSL is a very powerful and
complicated system. It uses X509 certificates for authentication, and supports
various algorithms, e.g. 3DES, AES, RC4 ... in its cipher suite. For more
information, please refer to the following wiki
pages:
Start TLS/SSL Server
Before starting the secured web server, the
following files are required:
|
1.
Program
file |
/flash/bin/boa-ssl |
|
2.
X509
certificate |
/flash/config/ssl/boa-ssl.crt |
|
3.
X509
private key |
/flash/config/ssl/boa-ssl.pem |
To start the web server, use ��boa-ssl�� command in the console or put it in the
/flash/config/autorun.ini script to load it automatically.
Make Certificates for Devices
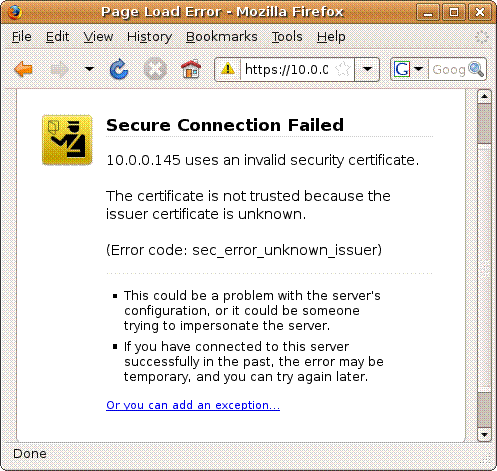
When using a browser to connect to the
device, a security alert will be shown. It��s normal, because the device��s
certificate is incorrect. and not signed by a trusted
CA (Certificate Authority).
The TLS/SSL authentication process requires
X509 certificates to identify the web server on a particular domain or IP
address. That is, a certificate works only at one domain or IP address. If the
IP address of the device is changed, the certificate should be reissued.
The X509 certificate included in the
release firmware is issued only valid for IP address 192.168.1.100, and it can
not be used for other IP addresses.
To make a valid certificate for the device,
in the directory ��app/x509�� of the release package, a shell script x509.sh is provided:
linux
run the x509.sh script in terminal:
Cygwin environment is required. To install Cygwin,
1.
run Setup.exe from www.cygwin.com
2.
install
all default packages and openssl
In Window��s command line, run ��bash x509.sh��.
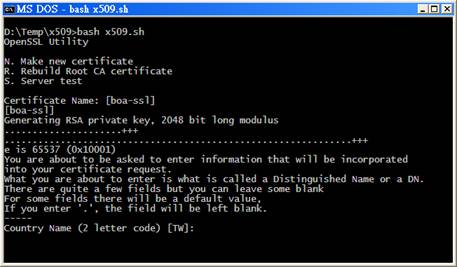
Select ��N�� to make a new certificate:
Except the IP address which should be set
to the devices�� IP address, other fields can be set to default values by
pressing ENTER.
|
OpenSSL Utility N.
Make new certificate R.
Rebuild S.
Server test Certificate
Name: [boa-ssl] [boa-ssl] Generating
RSA private key, 2048 bit long modulus ......................+++ ...+++ e
is 65537 (0x10001) You
are about to be asked to enter information that will be incorporated into your certificate request. What
you are about to enter is what is called a Distinguished Name or a DN. There
are quite a few fields but you can leave some blank For
some fields there will be a default value, If
you enter '.', the field will be left blank. ----- Country
Name (2 letter code) [TW]: State
or Province Name (full name) [ Locality
Name (eg, city) [ Organization
Name (eg, company) [ARM7 SSL Device]: Organizational
Unit Name (eg, section) [ARM7]: Domain or IP Address [192.168.1.100]: Device
IP Address Email
Address [admin@uClinux.dev]: Please
enter the following 'extra' attributes to
be sent with your certificate request A
challenge password []: An
optional company name []: Signature
ok subject=/C=TW/ST=Taiwan/L=Taipei/O=ARM7
SSL Device/OU=ARM7/CN=192.168.1.100/emailAddress=admin@uClinux.dev Getting
CA Private Key [boa-ssl.crt] generated ---
Press any key to continue --- |
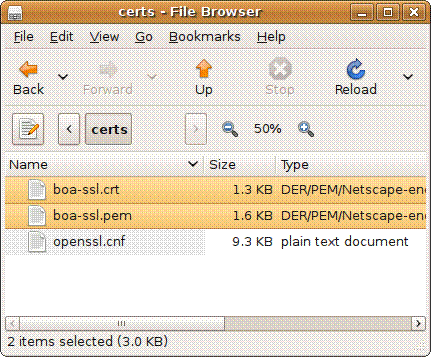
This will generate 2 valid certificate files: boa-ssl.crt and boa-ssl.pem.
Copy them into the device��s /flash/config/ssl directory and restart the boa-ssl server.
Install the CA (Certificate Authority) into Web
Browsers
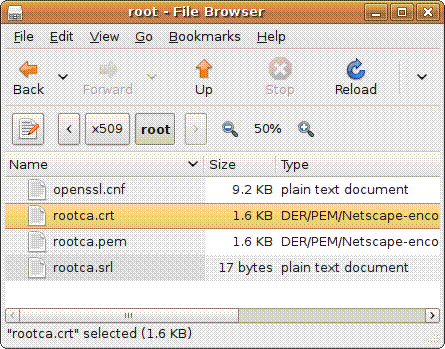
The root CA ��rootca.crt�� is stored in the
directory ��app/x509/root�� of the release package:
Microsoft
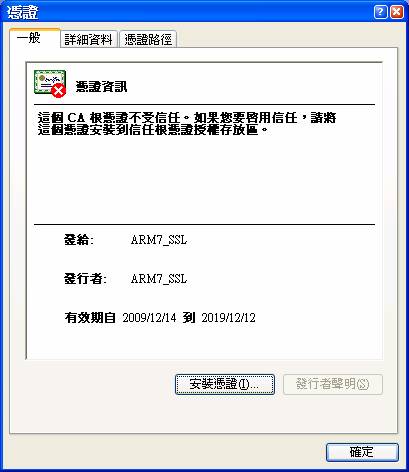
Windows IE:
Click the file ��rootca.crt�� with mouse in file manager,
the installation process will be initiated:
Mozilla Firefox
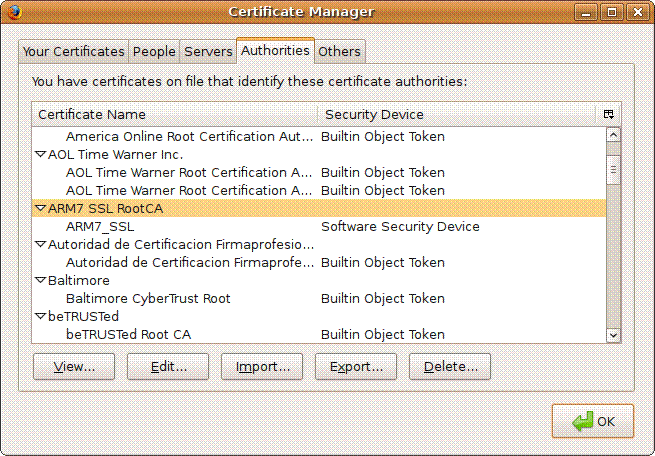
Go to [Firefox
Preference] [Advanced] [Encryption Tab] [View Certificates]
In the [Authorities] Tab, select [Import]
to install ��rootca.crt��
into Firefox as ��ARM7_SSL RootCA��.
Rebuild
If you need to rebuild your own private CA,
it is simpler than normal certificates. Run the x509.sh script, similar to the
procedure in making new certificate, select ��R�� to start the process and fill
the required fields:
|
OpenSSL Utility N.
Make new certificate R.
Rebuild S.
Server test Generating
RSA private key, 2048 bit long modulus ..........................+++ .........................................................................................+++ e
is 65537 (0x10001) You
are about to be asked to enter information that will be incorporated into your certificate request. What
you are about to enter is what is called a Distinguished Name or a DN. There
are quite a few fields but you can leave some blank For
some fields there will be a default value, If
you enter '.', the field will be left blank. ----- Country
Name (2 letter code) [TW]: State
or Province Name (full name) [ Locality
Name (eg, city) [ Organization
Name (eg, company) [ARM7 SSL RootCA]: Organizational
Unit Name (eg, section) [ARM7]: Common
Name (eg, YOUR name) [ARM7_SSL]: Email
Address [admin@uClinux.dev]: ---
Press any key to continue --- |
The files rootca.crt and rootca.pem will be generated under the ��x509/root�� directory.
Please note that a root CA is used to sign all issued certificates. After rebuilding the root CA, all subsequent certificates will be signed by this new root CA. To make this new CA trusted by browsers, the CA should be installed into browsers again.
Commercial
Certificates
There are commercial certificates available which are signed by trusted organizations that have been built into most browsers�� database, For example:
Verisign TW Price per domain (IP address): NT$18,000 / Year
Verisign US Price per domain (IP address) US$ 399 / year
GoDaddy US Price per domain (IP address) US$ 29.99 / Year
The only advantage using commercial certificates instead of private certificates is that users do not need to install a root CA into their browsers. But the cost seems too high and impractical for management in the intranet applications.